Copy Snapshots
Overview
The Copy Snapshots action allows you to duplicate EBS Snapshots to different regions or accounts. It provides flexibility with encryption: maintain the current key for encrypted snapshots or choose a new one. For unencrypted source snapshots, add encryption by selecting a KMS key.
This action is useful for disaster recovery, data management and ensuring data availability across AWS environments. It enables seamless duplication of EBS snapshots across regions or accounts. Additionally, it enhances security and compliance by enabling encryption for previously unencrypted snapshots.
Permissions
The Copy Snapshots action uses the following endpoints in AWS’s EC2 API to target and copy EBS Snapshots:
The following use cases do not require any new permissions:
- Copying unencrypted snapshots
- Copying and encrypting unencrypted snapshots
- Copying snapshots to a different region in the same AWS account
If these are your only scenarios then you do not need to use the AWS Console. Please return to GorillaStack and configure your rule.
The following use case does require new permissions:
- Copying encrypted snapshots to a different AWS account
These new permissions are specified in a key policy and an IAM policy in AWS. To protect your security, we do not ask to change these policies automatically on your behalf. Instead, you must update these policies yourself. Details for doing this via the AWS Console are below. These instructions assume you intend to re-encrypt your copied snapshots with a new key, as that is the most secure option.
Once you have updated these policies in AWS, the Copy Snapshots action will take care of the rest. This includes adding the destination account to the sharing permissions on the EBS Snapshot.
Key terms
- Source Account: the AWS account that you have linked to GorillaStack and which contains the snapshot that you want to copy
- Destination Account: the AWS account that you have linked to GorillaStack and to which you want to copy the snapshot from the source account
Step 1. Allow The Destination Account To Copy Shared Snapshots
- Log into the source account in the AWS Console
- Select KMS Key Management Service
- Select Customer Managed Keys
- Select the destination region
- Select the key you are willing to share with the destination account — if the snapshot is encrypted, this must be the key that was used to encrypt it
- If Switch To Policy View is visible, click it
- Click Edit
- Add a comma followed by a new line to the last statement in the
Statementarray - Add the following new permissions to the
Statementarray, after the comma - Replace
<<arn-of-gs-role-in-source-account>>with the actual ARN from GorillaStack’s Platforms page - Replace
<<arn-of-gs-role-in-destination-account>>with the actual ARN from GorillaStack’s Platforms page - Save
- Note the key’s ARN so you can use it later as
<<arn-of-key-in-source-account>>
The new permissions:
{
"Sid": "CopySnapshotsUseSourceKeyInSourceAccount",
"Effect": "Allow",
"Principal": {
"AWS": "<<arn-of-gs-role-in-source-account>>"
},
"Action": [
"kms:DescribeKey",
"kms:ReEncrypt*"
],
"Resource": "*"
},
{
"Sid": "CopySnapshotsUseSourceKeyInDestinationAccount",
"Effect": "Allow",
"Principal": {
"AWS": "<<arn-of-gs-role-in-destination-account>>"
},
"Action": [
"kms:CreateGrant",
"kms:Decrypt",
"kms:DescribeKey",
"kms:Encrypt",
"kms:GenerateDataKey*"
],
"Resource": "*",
"Condition": {
"Bool": {
"kms:GrantIsForAWSResource": "true"
}
}
}Step 2: Allow The Destination Account To Access The Snapshots Using The Shared Keys
- Log into the destination account in the AWS Console
- Select Identity & Access Management (IAM)
- Select Policies
- Click Create Policy
- Select JSON
- Add the following new permissions
- Change
<<arn-of-key-in-source-account>>to the key ARN you noted above - Change
<<region-of-key-in-source-account>>to the region string in the key ARN (e.g.us-east-2) - Save the policy with a meaningful name
- Select Roles within Identity & Access Management (IAM)
- Select your GorillaStack cross-account access role — the same one you see listed in GorillaStack’s Platforms page
- Add the new policy to the role
- Save
The new permissions:
{
"Version": "2012-10-17",
"Statement": [
{
"Sid": "CopySnapshotsUseSourceKeyInDestinationAccount",
"Effect": "Allow",
"Action": [
"kms:DescribeKey",
"kms:ReEncrypt*"
],
"Resource": "<<arn-of-key-in-source-account>>"
},
{
"Sid":
"CopySnapshotsAttachPersistentResourcesWithSourceKeyInDestinationAccount",
"Effect": "Allow",
"Action": [
"kms:CreateGrant",
"kms:Decrypt",
"kms:DescribeKey",
"kms:Encrypt",
"kms:GenerateDataKey*"
],
"Resource": "<<arn-of-key-in-source-account>>",
"Condition": {
"Bool": {
"kms:GrantIsForAWSResource": "true"
},
"ForAnyValue:StringEquals": {
"kms:ViaService": "ec2.<<region-of-key-in-source-account>>.amazonaws.com"
}
}
}
]
}Step 3. Configure GorillaStack
Log into GorillaStack and create a rule with a Copy Snapshots action.
Select your source account(s) in the rule context.
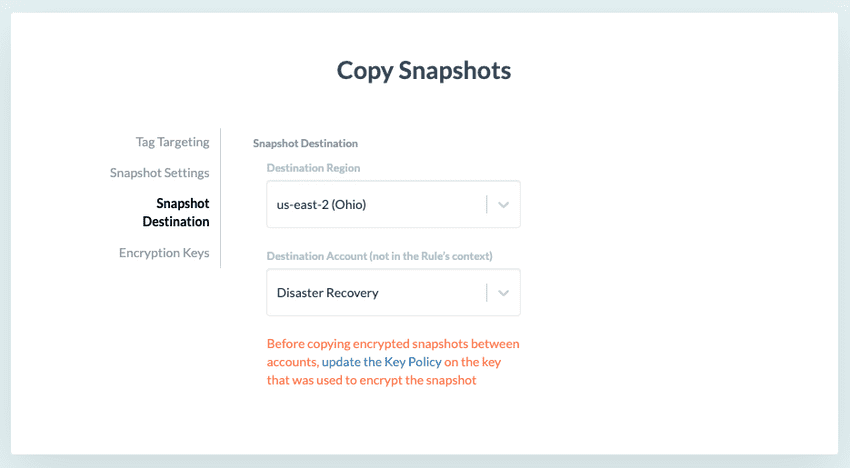
Note that your destination account must not be one of your source accounts.
Select your destination account in the Snapshot Destination panel of the Copy Snapshots action.