Notify on Azure Subscription Event
Overview
The Notify on Azure Subscription Event action promptly informs you of specific events from your Azure Subscription Event Grid Subscription or diagnostic logs on your Azure resources. By integrating this action, you efficiently convert these events into valuable notifications for quick response and effective management.
This action streamlines the process of staying updated on critical Azure events, ensuring that essential events are promptly received and addressed. It enhances your ability to respond to and manage these events in a timely and organized manner.
Use of this action in a rule
The Notify on Azure Subscription Event action must always be used in a rule with the Azure Subscription Event trigger, which takes responsibility for sourcing selected events from your Azure Subscription.
Note: the Run Now button is disabled on any rule that has the Notify on Azure Subscription Event action.
Turning events into notifications
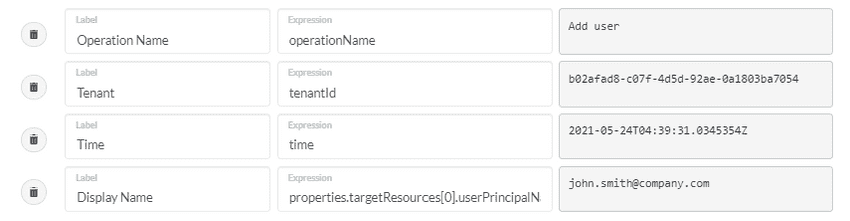
Provide JMESPath expressions to pluck values
from your Azure Subscription events. For example, the following expressions pluck key values from
an Add user event from Azure Active Directory diagnostic logs.
Don’t worry about any <no-value> messages that you might see. They just mean that
the sample event currently loaded in the Example Event box in the Notify on Azure Subscription Event action
screen does not contain any values that match your JMESPath Expressions. However, you can
replace any <no-value> messages with actual results by pasting an actual event of the
desired type into the Example Box. For example, an Add user event like
this one was loaded when creating the mappings shown above:
{
"time": "2021-05-24T04:39:31.0345354Z",
"resourceId": "/tenants/b02afad8-c07f-4d5d-92ae-0a1303ba7054/providers/Microsoft.aadiam",
"operationName": "Add user",
"operationVersion": "1.0",
"category": "AuditLogs",
"tenantId": "b02afad8-c07f-4d5d-92ae-0a1803ba7054",
"resultSignature": "None",
"durationMs": 0,
"callerIpAddress": "20.190.142.171",
"correlationId": "c8ee8788-22a6-4c6b-ba08-36c57939575c",
"Level": 4,
"properties": {
"id": "Directory_c8ee8788-22a6-4c6b-ba08-36c57939575c_47BWD_107340660",
"category": "UserManagement",
"correlationId": "c8ee8788-22a6-4c6b-ba08-36c57939575c",
"result": "success",
"resultReason": "",
"activityDisplayName": "Add user",
"activityDateTime": "2021-05-24T04:39:31.0345354",
"loggedByService": "Core Directory",
"operationType": "Add",
"initiatedBy": {
"user": {
"id": "c8559da2-cbfc-4302-aeec-c768edf33574",
"displayName": null,
"userPrincipalName": "admin@company.com",
"ipAddress": null,
"roles": []
}
},
"targetResources": [
{
"id": "0dcc3a70-fe1b-4e05-a256-a7cd7f303d03",
"displayName": null,
"type": "User",
"userPrincipalName": "john.smith@company.com",
"modifiedProperties": [
{
"displayName": "AccountEnabled",
"oldValue": "[]",
"newValue": "[true]"
},
{
"displayName": "DisplayName",
"oldValue": "[]",
"newValue": "[\"John Smith\"]"
},
{
"displayName": "MailNickname",
"oldValue": "[]",
"newValue": "[\"john.smith\"]"
},
{
"displayName": "StsRefreshTokensValidFrom",
"oldValue": "[]",
"newValue": "[\"2021-05-24T04:39:30Z\"]"
},
{
"displayName": "UserPrincipalName",
"oldValue": "[]",
"newValue": "[\"john.smith@company.com\"]"
},
{
"displayName": "UserType",
"oldValue": "[]",
"newValue": "[\"Member\"]"
},
{
"displayName": "Included Updated Properties",
"oldValue": null,
"newValue": "\"AccountEnabled, DisplayName, MailNickname, StsRefreshTokensValidFrom, UserPrincipalName, UserType\""
}
],
"administrativeUnits": []
}
],
"additionalDetails": [
{
"key": "User-Agent",
"value": "Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/90.0.4430.212 Safari/537.36"
}
]
}
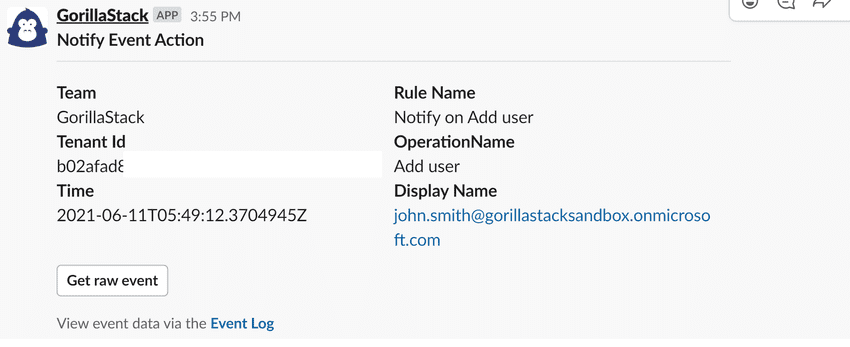
}Once you have saved the rule and Azure generates a matching event, you will receive a notification that looks like this: