Role Based Access Control (RBAC)
GorillaStack ships with three standard user roles: Admin, Member and Guest. When companies using GorillaStack have particular RBAC requirements we typically recommend creating custom Roles.
When creating a new Role, users can define inheritance between roles and define policies that either allow or deny privileges on different resources. For example, a team may decide that they only want to give their Developers read-only access, with additional privileges to manually execute their rules, as well as snooze/cancel privileges so that they can interact with schedule-based triggers. Using GorillaStack they could create a new role named 'Developer' which inherits from the Guest role, and includes an allow policy on Rules, allowing privileges of ManuallyExecute, Snooze and Cancel.
Creating a custom role
- First click the Roles link in the left nav for the User Management view
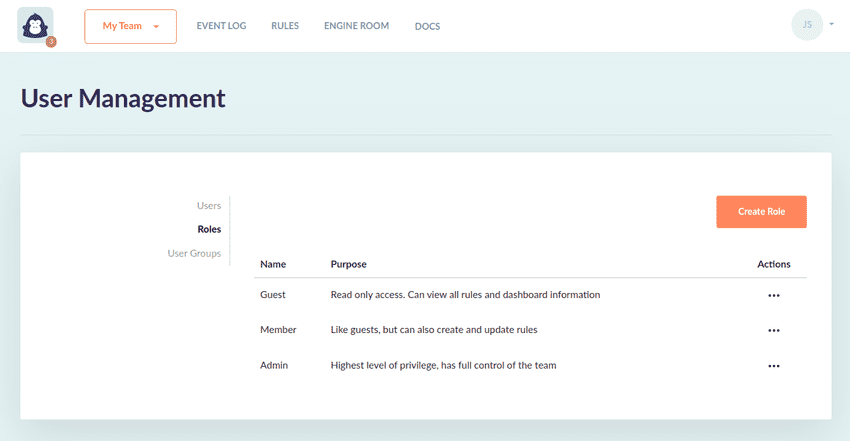
- Click Create Role
- Name your role and optionally add a description
- Define a parent role from which you want to inherit existing access policies
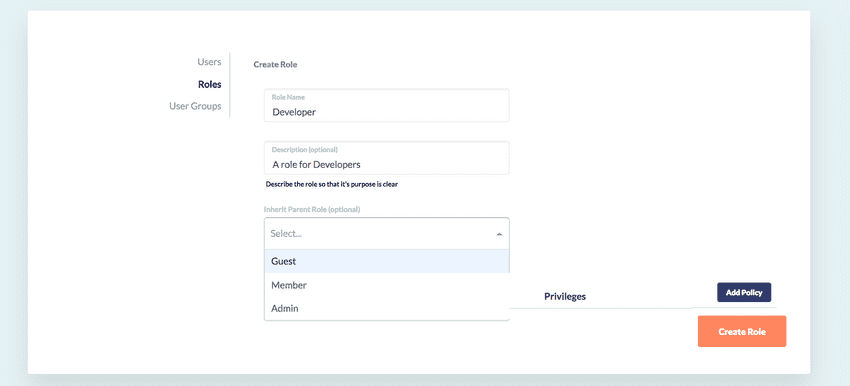
- Click Add Policy to add a policy to the custom Role
- Select
allowordenyand then a resource type and a combination of privileges for that resource that you wish to allow or deny over that given resource.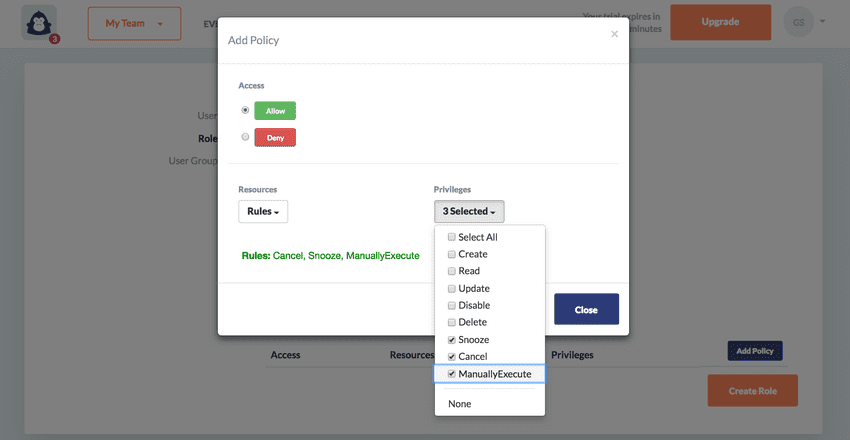
- Continue to add as many policies as you require to customize access control for users with this Role
- Click Create Role to complete the Role creation