Start Instances
Overview
The Start Instances action starts your EC2 Instances on demand.
Working in conjunction with the Stop Instances action, these actions automate EC2 instance management, help optimization of resource usage and costs, and give you the flexibility to scale your compute resources up or down as your workload demands.
Permissions
The action uses the following AWS EC2 API endpoints to target and start EC2 Instances:
Starting Instances with Attached Encrypted EBS Volumes
It is possible for an EC2 Instance to remain in a stopped state even if it is successfully targeted by the Start
Instances Action. The StartInstances endpoint, which is used by this action, can silently fail to start EC2 Instances
that have attached encrypted EBS Volumes.
Why Does this Happen?
The AWS Key Management Service (KMS) is leveraged to perform encryption on EBS Volumes.
Each KMS Customer Master Key (CMK) has a Key Policy which defines who has permission to use the CMK and what API actions a privileged entity can perform using the CMK.
How to Remedy the Issue?
- Determine which KMS CMKs are used to encrypt each EBS Volume attached to EC2 Instances which you are trying to start
- Update each CMK’s Key Policy, ensuring principal of least privilege is observed by utilizing the
kms:ViaServicecondition (see example below)
From the AWS KMS Best Practices whitepaper
{
"Sid": "Allow for EC2 Use",
"Effect": "Allow",
"Principal": {
"AWS": "arn:aws:iam::111122223333:root"
},
"Action": [
"kms:CreateGrant",
"kms:ListGrants",
"kms:RevokeGrant"
],
"Resource": "*",
"Condition": {
"StringEquals": {
"kms:ViaService": "ec2.<<region>>.amazonaws.com"
}
}
}The statement in this policy provides the specified IAM principal the ability to create, list, and revoke grants for Amazon EC2. Grants are used to delegate a subset of permissions to AWS services, or other principals, so that they can use your keys on your behalf. In this case, the condition policy explicitly ensures that only Amazon EC2 can use the grants. Amazon EC2 will use them to re-attach an encrypted EBS volume back to an instance if the volume gets detached due to a planned or unplanned outage. These events will be recorded within AWS CloudTrail when, and if, they do occur for your auditing.
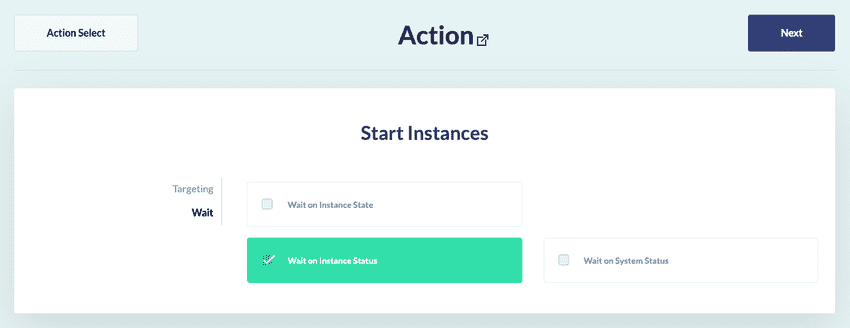
Wait
You may need the Start Instances action to confirm the targeted EC2 Instances have finish starting before moving onto the next action in a rule.
You can achieve this using the Start Instances action’s Wait panel, pictured:
If you select Wait on Instance State, the action will wait until the describeInstanceStatus endpoint returns
an instanceState of running.
If you select Wait on Instance Status, the action will wait until the describeInstanceStatus endpoint returns
an instanceStatus of ok, impaired or not-applicable.
If you select Wait on System Status, the action will wait until the describeInstanceStatus endpoint returns
a systemStatus of ok, impaired or not-applicable.